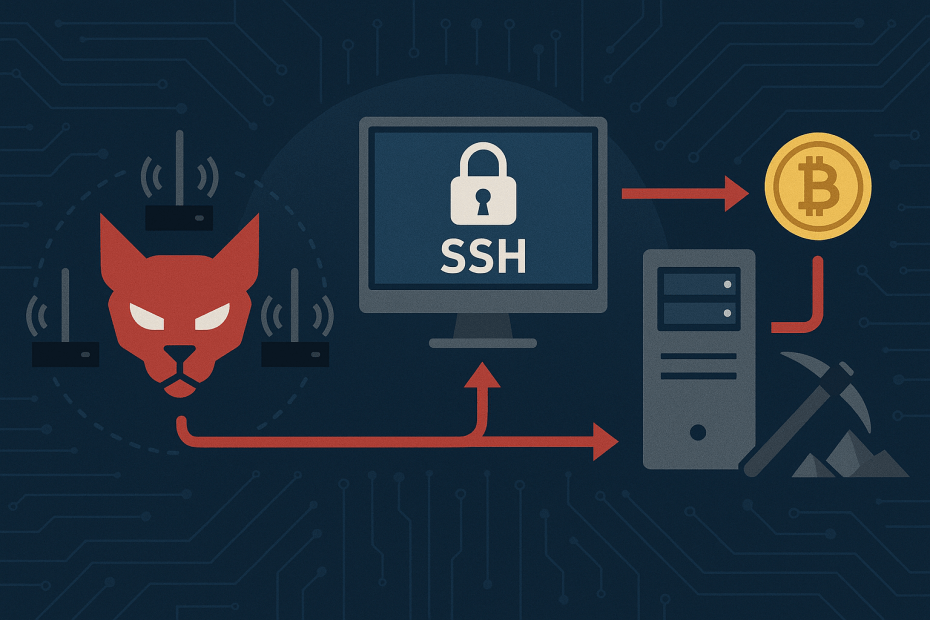
Internet of Things (IoT) devices powered by embedded Linux are becoming increasingly common in businesses, offering convenience but also expanding the cyberattack surface. Recently, cybersecurity researchers have uncovered a new botnet called PumaBot actively targeting Linux IoT devices to steal SSH credentials and use compromised systems for cryptocurrency mining. This emerging threat highlights the urgent need for small business owners to strengthen their IoT and SSH security measures.
What is PumaBot?
PumaBot is a sophisticated malware written in the Go programming language that conducts brute-force attacks to gain unauthorized access over SSH (Secure Shell) services running on Linux-based IoT devices. Rather than indiscriminately scanning the internet, PumaBot receives a curated list of IP addresses from a command-and-control (C2) server and attempts to brute force credentials, significantly increasing the efficiency and success of its attacks.
How Does PumaBot Operate?
- Target Acquisition: The malware fetches target IP addresses from an external server (notably ssh.ddos-cc[.]org) rather than scanning randomly.
- Credential Brute-Forcing: PumaBot attempts to crack SSH credentials by systematically trying passwords against open SSH ports.
- System Fingerprinting: It verifies system suitability by checking for honeypots or specifically targeting/excluding devices from certain manufacturers, such as “Pumatronix,” known for surveillance cameras.
- Persistence: Once access is granted, PumaBot installs itself disguised as legitimate system files like Redis (/lib/redis) and creates persistent services using systemd to survive reboots.
- Command Execution & Cryptocurrency Mining: Commands such as xmrig and networkxm are launched to mine cryptocurrency using the infected device’s resources illicitly.
- Credential Theft and Exfiltration: PumaBot also deploys a rootkit disguised as “pam_unix.so” to intercept and steal SSH credentials by monitoring login attempts and sending stolen data back to its C2 server.
The Broader Campaign and Worm-like Capabilities
Beyond brute-force attacks, PumaBot involves additional components to maintain control and spread itself, including:
- ddaemon: A backdoor that retrieves and executes further payloads.
- networkxm: Another SSH brute-force tool used to continue expanding the infection.
- Shell scripts like installx.sh and jc.sh that modify system files and aid persistence.
- A malicious pam_unix.so rootkit for credential theft.
- An exfiltration binary to send stolen credentials back to the attackers.
PumaBot’s abilities to automatically propagate through SSH brute-forcing give it worm-like characteristics, making it a rapidly evolving and persistent threat that can infiltrate entire networks of IoT devices.
Why Should Small Businesses Be Concerned?
Many small businesses rely on Linux-based IoT devices for surveillance, automation, or network services without fully understanding the security risks. Compromise by PumaBot could lead to:
- Data Breaches: Stolen SSH credentials could expose sensitive business information or provide a foothold for further attacks.
- Resource Hijacking: Your devices could be used to mine cryptocurrency for attackers, degrading performance and increasing electricity costs.
- Network Spread: PumaBot could use your network as a launchpad to attack other devices or businesses.
- Reputation Damage: Infected public-facing IoT devices might be flagged or blacklisted, resulting in loss of trust.
Protective Measures Against PumaBot and Similar Threats
Small business owners can take several proactive steps to defend against PumaBot and related cyber threats:
- Monitor SSH Logs: Regularly check for unusual or repeated failed login attempts.
- Use Strong, Unique Credentials: Avoid default or weak passwords; implement SSH key-based authentication.
- Limit SSH Access: Restrict SSH login to specific IP addresses or use VPNs to minimize exposure.
- Audit systemd Services: Review for suspicious services named similarly to legitimate ones (e.g., redis.service or mysqI.service).
- Deploy Firewalls and Filtering: Use firewall rules to limit access to ports and filter HTTP requests with abnormal headers (e.g., “X-API-KEY: jieruidashabi”).
- Update and Patch Devices: Regularly apply security updates to your IoT devices and Linux systems.
- Consider Professional Security Services: Partner with cybersecurity experts to implement continuous monitoring and threat detection tailored to your environment.
For tailored cybersecurity solutions, small business owners can explore professional services such as those found at CyberDef Solutions that specialize in protecting IoT and Linux infrastructures.
Conclusion
The PumaBot botnet exemplifies the increasing sophistication of threats targeting Linux IoT devices and the critical importance of SSH security. Small businesses must remain vigilant, adopting strong security practices to prevent unauthorized access and protect their digital assets. By staying informed and taking proactive measures, you can safeguard your business from becoming part of such malicious botnet campaigns.
Need expert cybersecurity assistance? Contact CyberDef today for robust, affordable protection tailored to your business needs.