Growing cyberthreats lead to serious financial impact
Almost half of businesses believe that scope of cyberthreats is evolving and growing faster than they can respond
Most of organizations have already suffered devastating losses from cyberattacks
The average cost to recover a business from a disruptive system breach
Uncompromising against threats
We extend the regular EDR capabilities with advanced response features, in-depth event analysis and contextualization, and SOAR-like automation.
Seamless integration into your environment
Neither your business, nor your protection can afford to wait. We take care of your defenses quickly and easily, allowing you to focus on what’s important.
Frequently Asked Questions
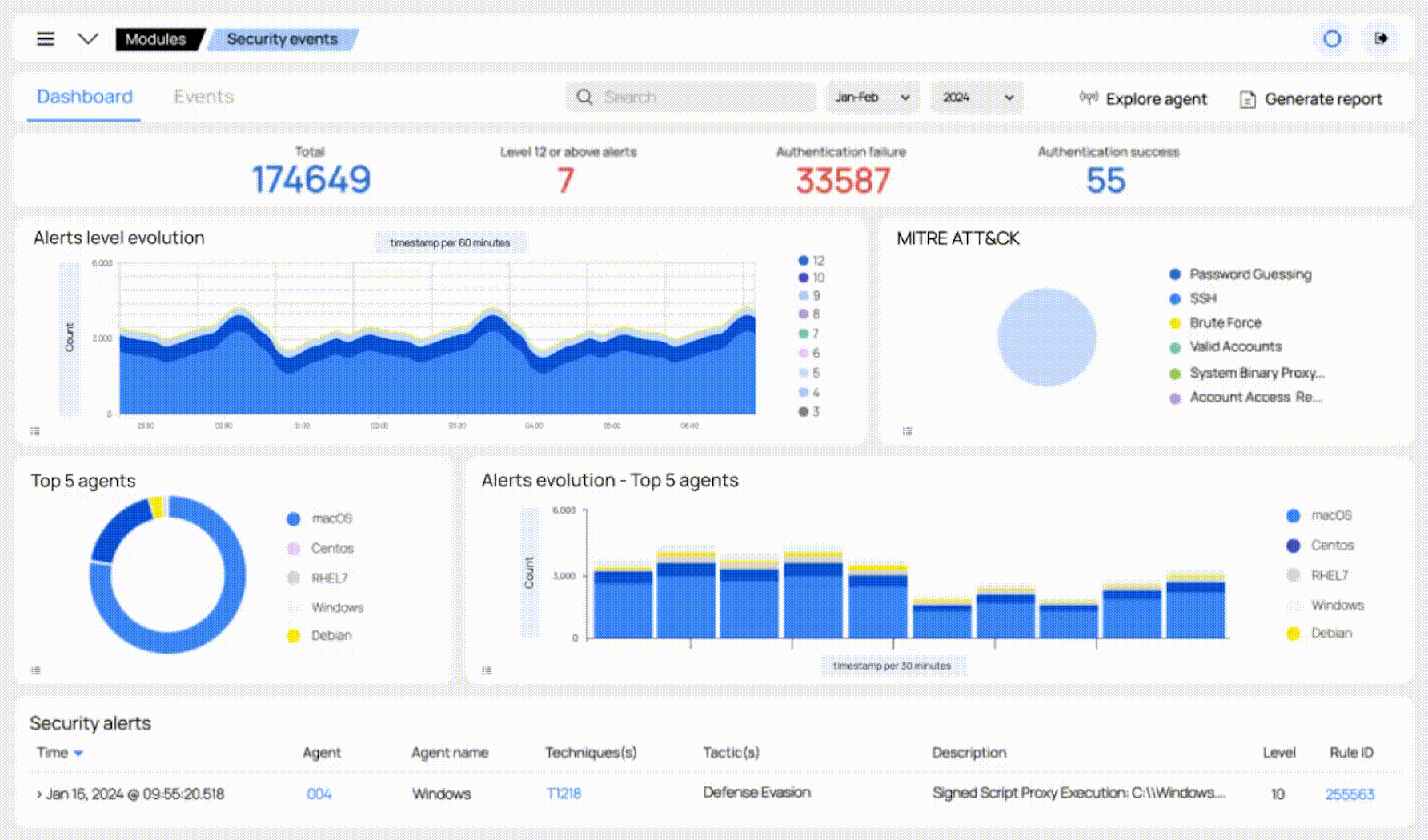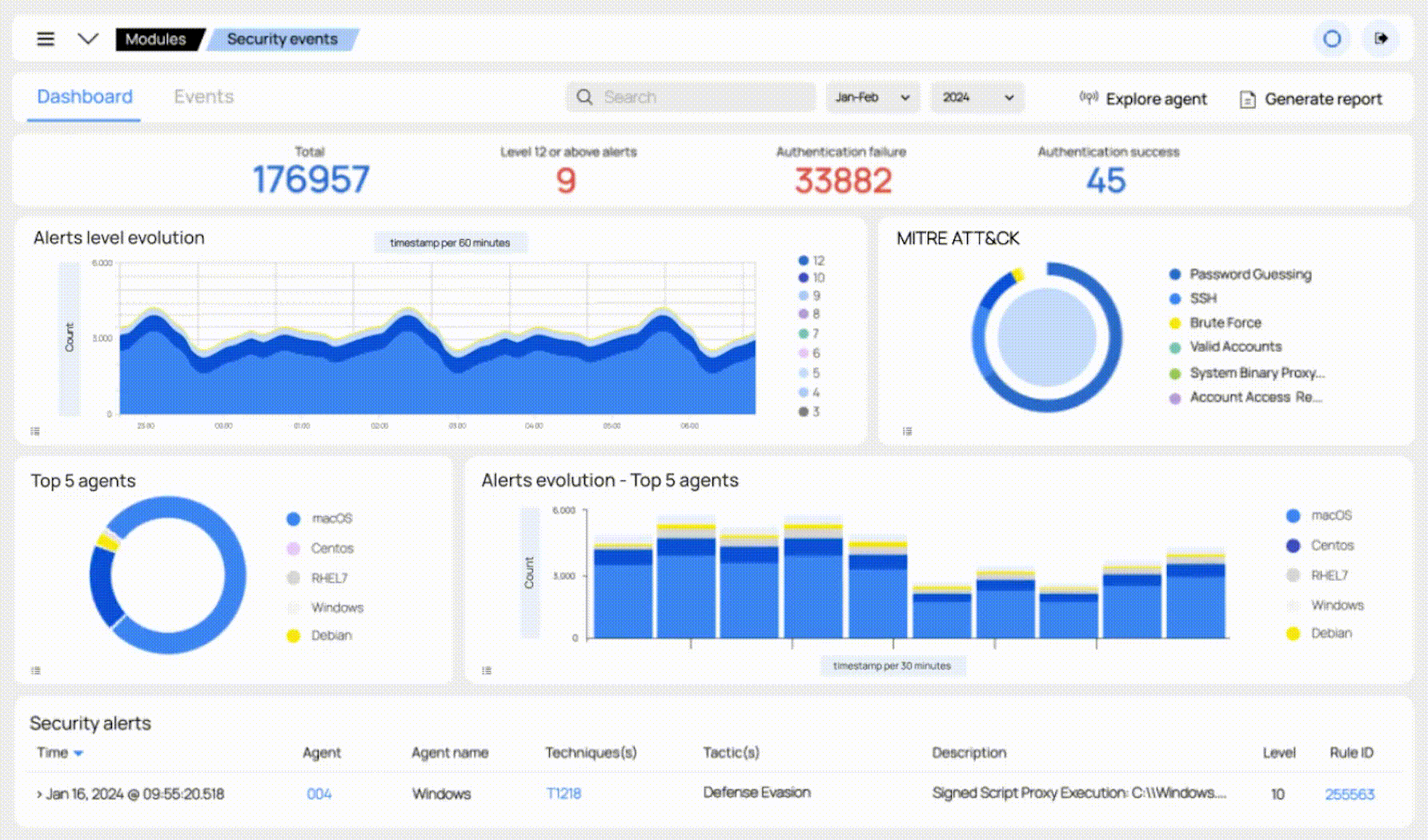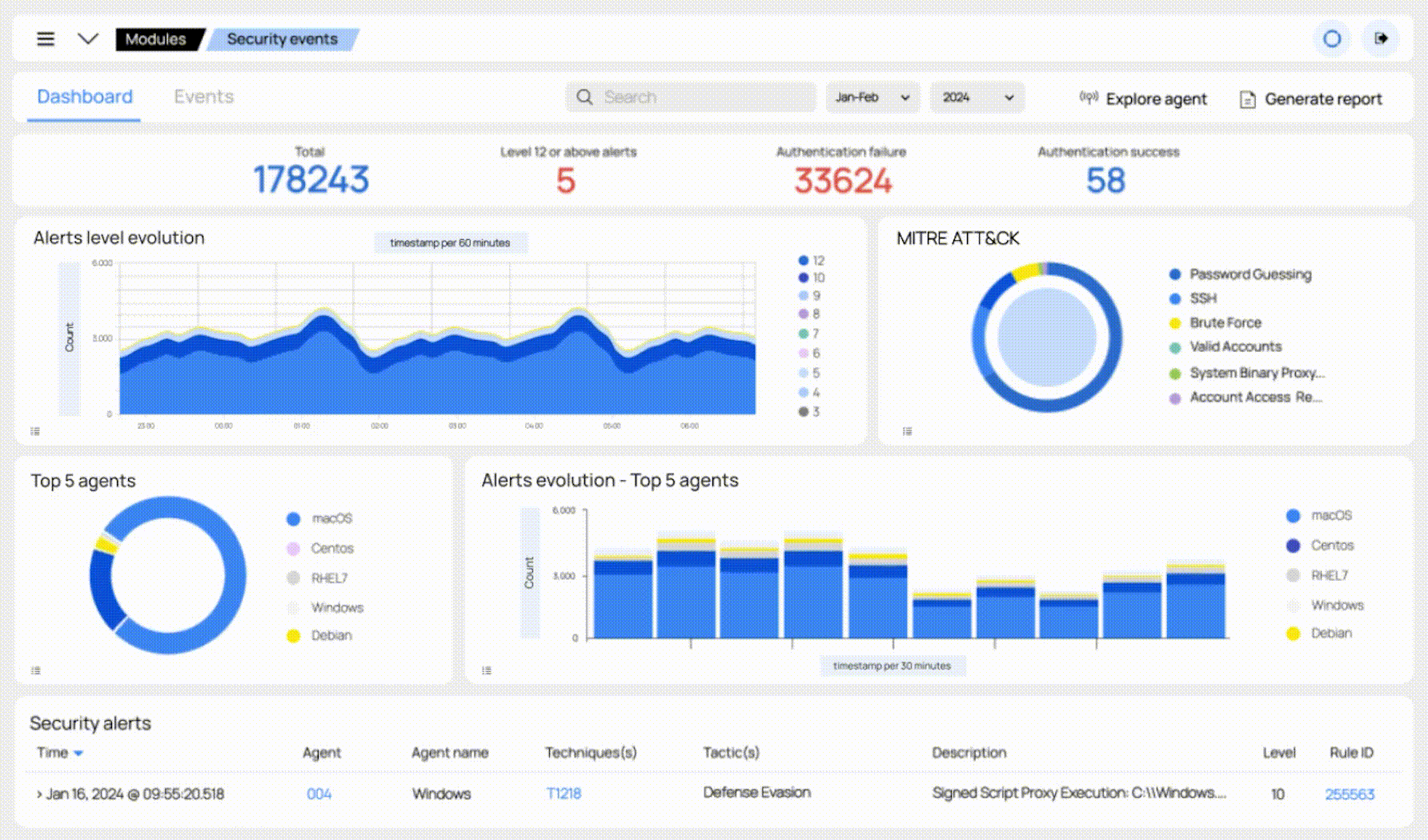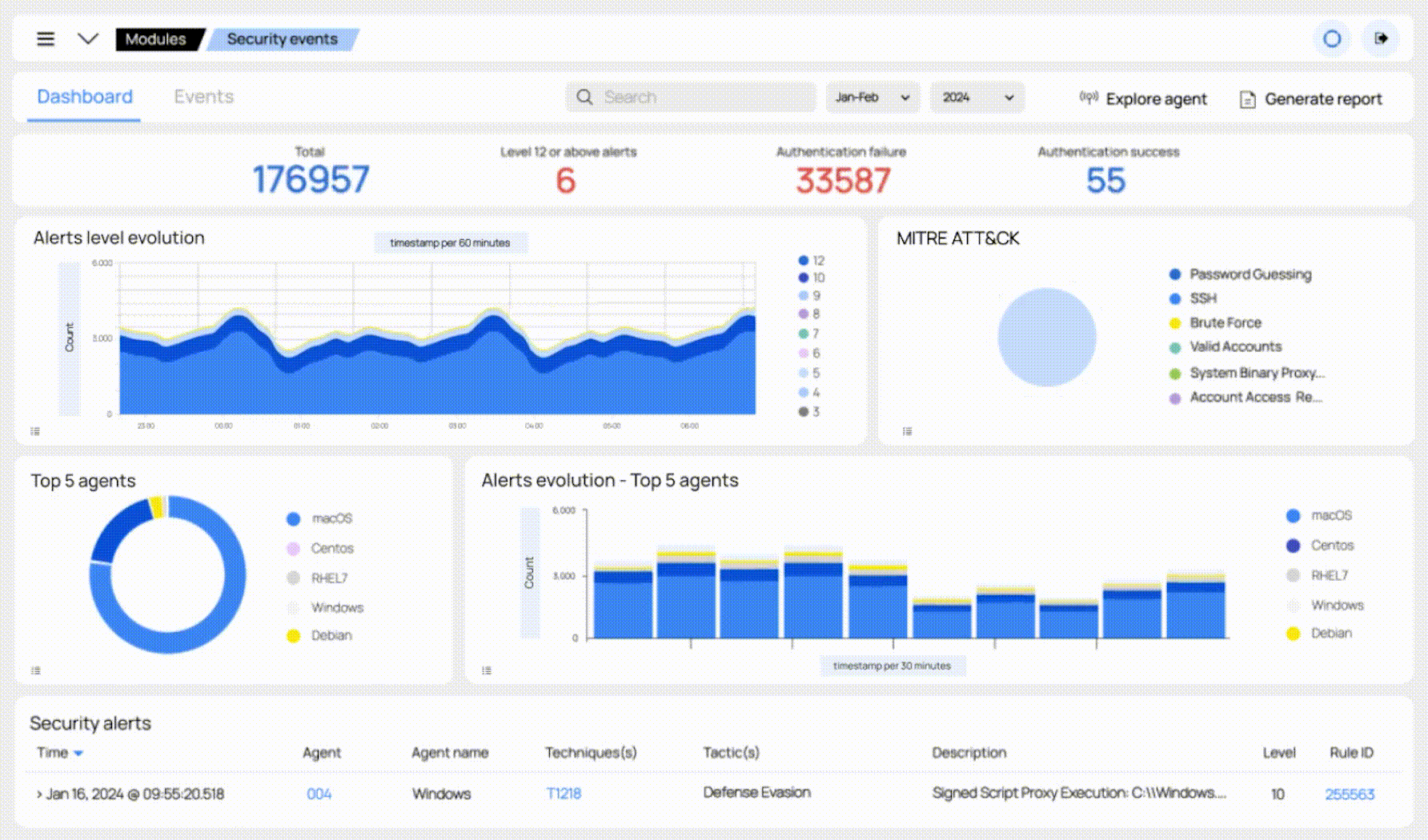
Our solution can automatically remediate most threats. For the rest, our security team of specialists will triage and analyze the alert, and act upon the results. You will receive reports and beautiful visualizations in the form of dashboards.
Continuous vulnerability scanning and system auditing are keys to staying out of reach from attackers. On top of that, we’re constantly updating our rules to, making sure you’re always protected.
Monitor access to your cloud and on-prem resources and block unauthorized actions. Control your environments with ease – access to sensitive data, application storage and more.